- 发帖可能变空内容,邪门暂不知所以然
- 『稷下学宫』新认证方式,24年网站打算和努力目标
主题:【原创】纯技术分析贴,是谁封了ccthere.com? -- 江阔云低
看到河里有人讨论这个话题,今天上班不忙,在公司做了个测试。
测试工具:snoop command
测试步骤:
Step 1: 执行以下命令:
bash-3.00# # nslookup
> ccthere.com
Server: xxxxxxx
Address: xxxxxxx
Non-authoritative answer:
Name: ccthere.com
Address: 68.233.230.142
>
DNS解析没有问题
bash-3.00# snoop -d hme -o snoop.out
Step 2: 用firefox访问ccthere.com,结果如图:
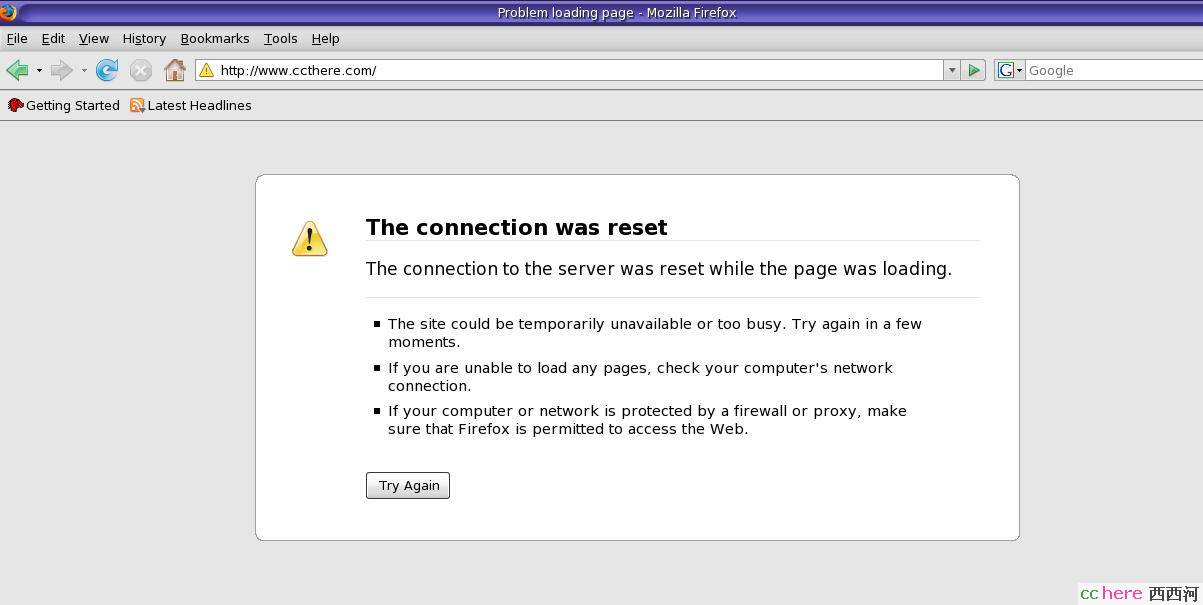
Step 3:
^C 得到snoop结果。
snoop 解析:
bash-3.00# snoop -i snoop.out -ta -V tcp port 80 |more
________________________________
1 14:49:11.27006 myhost -> ccthere.com ETHER Type=0800 (IP), size = 66
bytes
1 14:49:11.27006 myhost -> ccthere.com IP D=68.233.230.142 S=xxx.xxx.xxx.xxx LEN=52, ID=31942, TOS=0x0, TTL=64
1 14:49:11.27006 myhost -> ccthere.com TCP D=80 S=32971 Syn Seq=537354463 Len=0 Win=49640 Options=<mss 1460,nop,wscale 0,nop,nop,sackOK>
1 14:49:11.27006 myhost -> ccthere.com HTTP C port=32971
________________________________
2 14:49:11.69009 ccthere.com -> myhost ETHER Type=0800 (IP), size = 60
bytes
2 14:49:11.69009 ccthere.com -> myhost IP D=xxx.xxx.xxx.xxx S=68.233.230.142 LEN=44, ID=0, TOS=0x0, TTL=43
2 14:49:11.69009 ccthere.com -> myhost TCP D=32971 S=80 Syn Ack=537354464 Seq=2971482276 Len=0 Win=5840 Options=<mss 1380>
2 14:49:11.69009 ccthere.com -> myhost HTTP R port=32971
________________________________
3 14:49:11.69014 myhost -> ccthere.com ETHER Type=0800 (IP), size = 54
bytes
3 14:49:11.69014 myhost -> ccthere.com IP D=68.233.230.142 S=xxx.xxx.xxx.xxx LEN=40, ID=31943, TOS=0x0, TTL=64
3 14:49:11.69014 myhost -> ccthere.com TCP D=80 S=32971 Ack=2971482277
Seq=537354464 Len=0 Win=49680
3 14:49:11.69014 myhost -> ccthere.com HTTP C port=32971
________________________________
从前三个包可以看出从客户端(我本地)到server(ccthere.com),tcp 三次握手完成,建立连接。
-------------------------
4 14:49:11.69027 myhost -> ccthere.com ETHER Type=0800 (IP), size = 452 bytes
4 14:49:11.69027 myhost -> ccthere.com IP D=68.233.230.142 S=xxx.xxx.xxx.xxx LEN=438, ID=31944, TOS=0x0, TTL=64
4 14:49:11.69027 myhost -> ccthere.com TCP D=80 S=32971 Push Ack=2971482277 Seq=537354464 Len=398 Win=49680
4 14:49:11.69027 myhost -> ccthere.com HTTP GET / HTTP/1.1
________________________________
第四个包开始客户端向http server要求内容。
---------------------------------
5 14:49:11.82236 ccthere.com -> myhost ETHER Type=0800 (IP), size = 60
bytes
5 14:49:11.82236 ccthere.com -> myhost IP D=xxx.xxx.xxx.xxx S=68.233.230.142 LEN=40, ID=27586, TOS=0x0, TTL=238
5 14:49:11.82236 ccthere.com -> myhost TCP D=32971 S=80 Rst Ack=537354464 Seq=2971482277 Len=0 Win=3016
5 14:49:11.82236 ccthere.com -> myhost HTTP R port=32971
________________________________
6 14:49:11.82236 ccthere.com -> myhost ETHER Type=0800 (IP), size = 60
bytes
6 14:49:11.82236 ccthere.com -> myhost IP D=xxx.xxx.xxx.xxx S=68.233.230.142 LEN=40, ID=27614, TOS=0x0, TTL=238
6 14:49:11.82236 ccthere.com -> myhost TCP D=32971 S=80 Rst Ack=537354464 Seq=2971483737 Len=0 Win=3017
6 14:49:11.82236 ccthere.com -> myhost HTTP R port=32971
________________________________
7 14:49:11.82248 ccthere.com -> myhost ETHER Type=0800 (IP), size = 60
bytes
7 14:49:11.82248 ccthere.com -> myhost IP D=xxx.xxx.xxx.xxx S=68.233.230.142 LEN=40, ID=27656, TOS=0x0, TTL=238
7 14:49:11.82248 ccthere.com -> myhost TCP D=32971 S=80 Rst Ack=537354464 Seq=2971486657 Len=0 Win=3018
7 14:49:11.82248 ccthere.com -> myhost HTTP R port=32971
________________________________
对包4的请求,包5,6,7的内容来看,似乎是http server向客户端回送了三个rst/ack 包, 阻断了连接。也就是浏览器返回的画面结果。
当然,这个rest(重置连接)肯定不是铁手大人的web服务器发出的。理论上来讲,从web server到我本地,中间经过的网络设备上(ISP)都有可能做手脚。
谁干的呢?
我用Rst Ack GFW做关键字 搜索了一下。
下面的link里有一些对GFW的阻断特征相关的讨论。
看完以后,谁是最大的嫌疑呢,就不用多说了吧。呵呵
- 相关回复 上下关系8
🙂【原创】纯技术分析贴,是谁封了ccthere.com?
🙂看来这是专业技术的问题,我不太懂。 缤纷落叶 字0 2010-10-29 06:32:52
🙂看到楼下有人看不明白的,试着帮忙翻译一下 13 猪头笨笨 字3996 2010-09-14 02:05:16
🙂为看不明白而花,呵呵 1 做客地球 字150 2010-09-13 18:42:25
🙂现在不是有个西厢计划 清徽 字28 2010-09-11 08:28:23
🙂这个分析靠谱! 一条溺水的鱼 字55 2010-07-15 22:45:22